Cyber Threat Monitoring
We implement robust cyber threat monitoring that allow us to detect and respond to threats more quickly, reducing the risk of data breaches, financial losses, and reputational damage. This continuous vigilance is essential for maintaining a strong security posture in the face of evolving cyber threats.
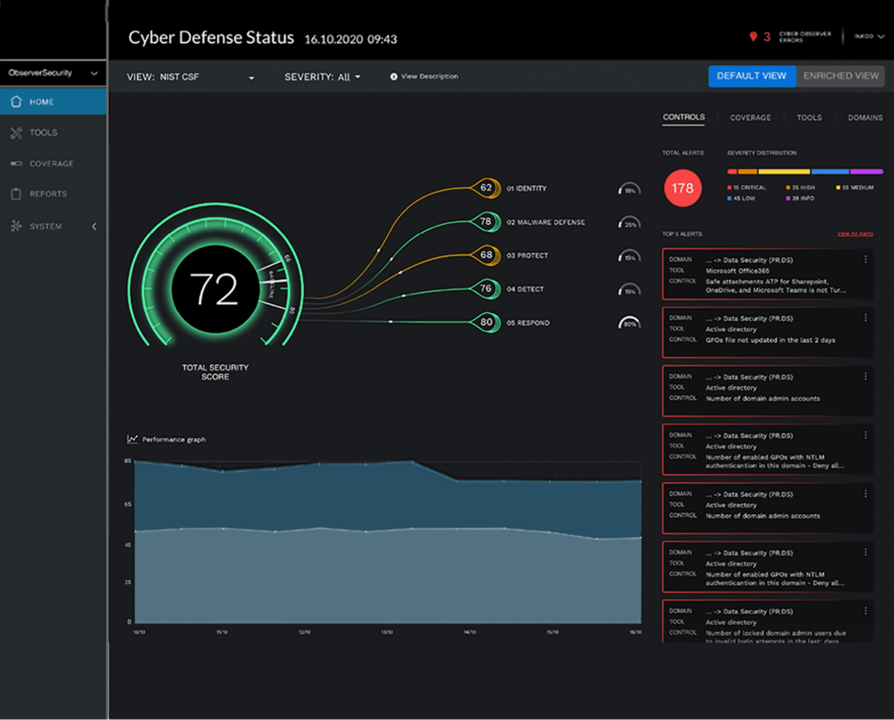
Our key components of cyber threat monitoring include:
1Network Monitoring
Continuously analyzing network traffic for unusual patterns or behaviors that may indicate a cyber threat. This includes monitoring for unauthorized access attempts, data exfiltration, and other suspicious activities.
2Endpoint Monitoring
Keeping an eye on endpoints (such as laptops, desktops, servers, and mobile devices) to detect signs of malware, unauthorized software installations, and other threats. Endpoint detection and response (EDR) tools are commonly used for this purpose.
3Log Analysis
Collecting and analyzing logs from various systems, applications, and devices to identify anomalies or indicators of compromise. Security information and event management (SIEM) systems play a crucial role in aggregating and analyzing log data.
4Threat Intelligence
Leveraging threat intelligence feeds to stay informed about the latest cyber threats, vulnerabilities, and attack techniques. This information helps security teams anticipate and defend against emerging threats.
5Behavioral Analytics
Using advanced analytics and machine learning to establish baseline behaviors for users and systems. Deviations from these baselines can indicate potential threats that require further investigation.
6Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS)
Deploying IDS and IPS to detect and block malicious activities on the network. IDS monitors and alerts on suspicious activities, while IPS can take automated actions to prevent threats.
7Vulnerability Scanning
Regularly scanning the IT environment for known vulnerabilities that could be exploited by attackers. This helps in timely patching and remediation efforts.
8User Activity Monitoring
Tracking user actions to detect insider threats or compromised accounts. This includes monitoring for unusual login patterns, data access, and changes to critical systems.
9Incident Response
Establishing protocols for responding to detected threats. This involves investigating alerts, containing the threat, eradicating malicious activities, and recovering affected systems.
10Reporting and Alerts
Generating real-time alerts and detailed reports on detected threats and security incidents. These insights help security teams prioritize their response efforts and communicate effectively with stakeholders.
